Cybersecurity & Data Privacy – Two Sides of the Same Coin
 https://www.techtarget.com/whatis/definition/Confidentiality-integrity-and-availability-CIA
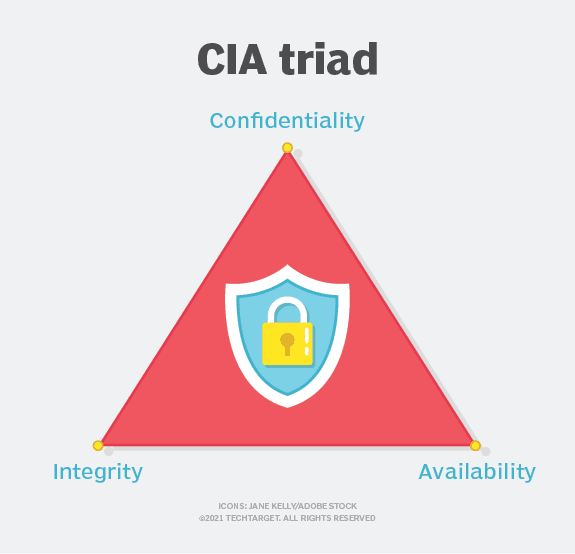
https://www.techtarget.com/whatis/definition/Confidentiality-integrity-and-availability-CIAIn information security, we often talk about the CIA Triad, but you may not know it’s also an important part of data privacy. No, this is not yet another blog post from my esteemed colleague from the three letter agency.
Instead, the CIA Triad refers to the 3 main tenets of information security: confidentiality, integrity, and availability.
Data Privacy & the CIA Triad
Let’s drive down to each guiding principle:
Confidentiality – Measures designed to protect sensitive information from unauthorized access.
Integrity – Involves maintaining the consistency, accuracy, and trustworthiness of data over its life cycle (protecting data from unauthorized manipulation at rest, in transit, etc.)
Availability – Ensures that data is consistently and readily accessible to authorized users.
The guiding principles above, form the foundation of the overall objectives of information security:
- ensuring that sensitive data is adequately protected,
- is free from unauthorized manipulation, and
- is available to authorized parties
When all three tenets of the triangle stand strong, security is well equipped to handle threats and incidents.
In this particular post, I would like to focus on the concept of confidentiality and its corollary, privacy, as it relates to information security.
What is Confidentiality? How does it relate to Privacy?
Confidentiality protects sensitive information from unauthorized access. Privacy is similar to confidentiality, but is specific to personal data, and not the super set of “sensitive data.”
For example, specific business information such as a credit card number or corporate financial information is typically deemed confidential. Employee or customer data such as name, birthdate, address, email, phone number, etc. are specifically part of data associated with privacy. Although information security and privacy are often used interchangeably, they are related, but not the same.
What’s with all the acronyms in Data Privacy?
As mentioned previously, privacy data is usually associated with individual data. There are numerous regulations globally that provide for individual data privacy rights such as GDPR (General Data Protection Regulation), in the EU and UK, CCPA (California Consumer Privacy Act) and the HIPAA Privacy Rule are all examples of privacy regulations that companies can be subject to.
GDPR, CCPA, HIPAA. Which one applies to my business?
GDPR provides individuals the right to be forgotten by a company, to request the deletion of their data from a company, and to prohibit a company from processing their data (right to object)
CCPA The California Consumer Privacy Act of 2018 (CCPA) gives consumers more control over the personal information that businesses collect about them and the CCPA regulations provide guidance on how to implement the law. This landmark law secures new privacy rights for California consumers, including:
- The right to know about the personal information a business collects about them and how it is used and shared;
- The right to delete personal information collected from them (with some exceptions);
- The right to opt-out of the sale of their personal information; and
- The right to non-discrimination for exercising their CCPA rights.
The HIPAA Privacy Rule establishes national standards to protect individuals’ medical records and other individually identifiable health information (collectively defined as “protected health information”) and applies to health plans, health care clearinghouses, and those health care providers that conduct certain health care transactions electronically.
The rule requires appropriate safeguards to protect the privacy of protected health information and sets limits and conditions on the uses and disclosures that may be made of such information without an individual’s authorization. The rule also gives individuals rights over their protected health information, including rights to examine and obtain a copy of their health records, to direct a covered entity to transmit to a third party an electronic copy of their protected health information in an electronic health record, and to request corrections.
How can a company effectively implement safeguards per the above privacy regulations?
By starting with cybersecurity. Companies start with a set of privacy policies and procedures, but eventually rely on information security controls to comply with privacy regulations.
A hypothetical, example of this at work. A privacy policy might require the company obfuscate protected health information. The security control that enables compliance with said policy is a procedure that requires protected health data be encrypted, at rest and in transit.
Encryption and Identity and Access Management controls support privacy objectives by ensuring data is protected and is only accessible by authorized individuals.
In closing, security and privacy are not synonymous, but are deeply intertwined as in the digital age, you cannot have privacy without security.
A Virtual Privacy Officer (vPO) can help you interpret confusing standards, understand disclosure procedures and reorganize resources already available to earn compliance. Get in touch to discover how we can simplify data privacy for you and your organization.



