Elevate Your Cybersecurity with Enclave: The Ultimate Solution for NSA's Zero Trust Recommendations
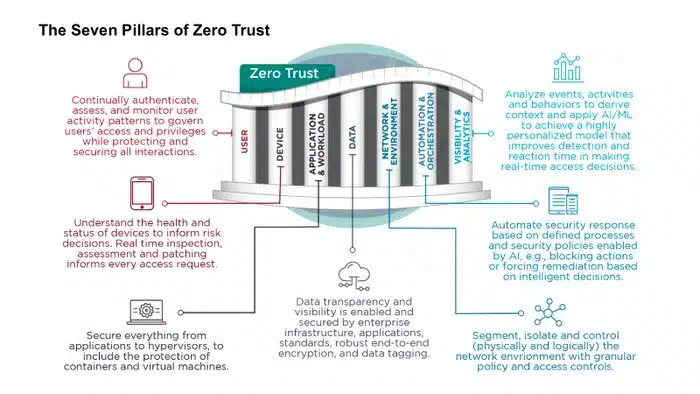
In the realm of cybersecurity, the landscape is perpetually evolving, compelling organizations to continually reassess and fortify their defenses against increasingly sophisticated threats. Recent guidance from the National Security Agency (NSA) underscores the pivotal role of Zero Trust Network Access (ZTNA) frameworks in safeguarding sensitive information and systems. Among the myriad of solutions vying to meet these stringent standards, Enclave emerges as a beacon of innovation, perfectly aligned with the NSA’s best-practice recommendations. This blog delves into the core aspects of Enclave and elucidates how it stands as the quintessential tool for navigating the complexities of modern cybersecurity challenges.
Understanding NSA’s Zero-Trust Recommendations
The Importance of Network Segmentation
The NSA’s latest Cybersecurity Information Sheet (CIS) emphasizes the critical need for organizations to segment their networks as a foundational element of a Zero Trust architecture. This segmentation serves as a robust barrier, restricting unauthorized access to sensitive data and thereby mitigating the risk of breaches. As reported by Dark Reading, the NSA’s guidance serves as a beacon for both defense-related and civilian industries in bolstering their cybersecurity defenses. Enclave’s microsegmentation capabilities resonate with this principle, offering a streamlined and effective approach to creating secure, isolated environments within an organization’s network.
Visibility and Rapid Isolation of Malicious Behavior
A core tenet of the NSA’s guidance is the concept of “visibility with context,” which enables the identification and isolation of malicious activities before they escalate into full-fledged breaches. Enclave’s architecture is designed to provide this level of insight, facilitating swift responses to potential threats and reinforcing the security posture of organizations.
Enclave: Tailored to NSA’s Zero Trust Framework
Seamless Integration with Zero Trust Principles
Enclave’s design philosophy is inherently aligned with the NSA’s Zero Trust framework, incorporating all the essential elements to support a robust cybersecurity strategy. By leveraging overlay networks, firewalls, and a Zero Trust permissions model, Enclave ensures that access to network resources is tightly controlled and monitored, adhering to the principle of least privilege access.
Simplifying the Complexity of Network Segmentation
One of the challenges highlighted in the NSA’s guidance is the complexity involved in implementing network segmentation, particularly in environments that have evolved organically over time. Enclave addresses this challenge head-on, offering a user-friendly platform that simplifies the creation and management of microsegments. This ease of use does not come at the expense of security, as Enclave employs stringent firewall rules and encryption to protect communications between nodes.
The Strategic Advantages of Enclave
Accelerating Incident Response Times
In the event of a security incident, time is of the essence. Enclave’s capabilities in isolating segments of the network can significantly reduce the time required to contain breaches. This rapid response capability is crucial in minimizing the impact of an attack and protecting against the lateral movement of adversaries within the network.
Enhancing Situational Awareness
Enclave’s comprehensive management console provides organizations with a clear overview of their network’s security posture. This enhanced situational awareness is invaluable for detecting potential vulnerabilities and responding to threats with precision and agility.
Implementing Enclave in Your Cybersecurity Strategy
Integrating Enclave into your cybersecurity framework is a strategic move that can elevate your organization’s defense mechanisms in line with the NSA’s Zero Trust recommendations. The platform’s focus on micro-segmentation, combined with its adherence to Zero Trust principles, makes it an indispensable tool for organizations seeking to fortify their cybersecurity infrastructure.
Flexible Deployment for Diverse Environments
Enclave’s flexibility in supporting both agent-based and agentless deployments ensures that it can be seamlessly integrated into a wide range of environments. Whether managing access for managed or unmanaged devices, or facilitating third-party access, Enclave offers a tailored solution that meets the specific needs of your organization.
Streamlining Compliance and Enhancing Security Posture
By aligning with the NSA’s Zero Trust guidelines, Enclave not only strengthens your organization’s security posture but also streamlines compliance with industry standards and regulations. This dual benefit is a testament to Enclave’s effectiveness as a comprehensive cybersecurity solution.
Discover the Power of Enclave
As cyber threats continue to evolve, the need for robust, adaptable, and efficient cybersecurity solutions has never been greater. Enclave stands at the forefront of this challenge, offering a powerful platform that embodies the principles of Zero Trust as recommended by the NSA. If your organization is seeking to enhance its cybersecurity measures, reduce the risk of breaches, and streamline compliance efforts, then Enclave is the solution you’ve been looking for.
Experience firsthand how Enclave can transform your organization’s security landscape. Schedule a demo today and take the first step towards a more secure, resilient, and compliant future. With Enclave, elevate your cybersecurity to meet and exceed the NSA’s best-practice recommendations, ensuring your network remains impervious to the ever-changing threat landscape.


