The Problem with Phishing
How I learned to stop worrying and just blame the victim
Key Takeaways
- Focus on stopping malicious email not blaming those who click
- Training alone is not enough to protect you from phishing attacks
- Stop sending mixed messages – don’t click on links… unless they’re from us
- Implement strong technical controls in your email gateway
- Review messages that slip through to improve your protections
- Consider eliminating internal email entirely
Introduction
Phishing attacks continue to be one of the most common and persistent security threats to every organization. The Cost of a Data Breach Report, 2024 by IBM reported that:
“For the 2nd year in a row, phishing and stolen or compromised credentials were the 2 most prevalent attack vectors. […] Phishing came in a close second, at 15% of attack vectors, but in the end cost more, a USD 4.88 million”
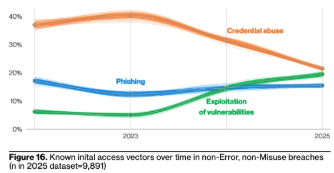
This aligns with the Verizon 2025 Data Breach Investigations Report which shows that Phishing attacks are one of the top initial or primary attack vector and remain constant at around 15% of all data breaches.
One reason why phishing attacks remain so costly is that we focus:
“Why did they click on that?”
This one question drives our obsession with user training and email simulations but it’s the wrong question. We should be asking:
“Why did they receive that message?”
Training our way to failure
Organizations typically respond to phishing threats through user-focused interventions including mandatory security training, phishing simulations, and incident-based education. This approach assumes that user education can mitigate social engineering techniques designed to exploit human psychology and mimic legitimate business communications, attacks which have been refined over the past decade and enhanced using recent developments in AI. These training programs can get click through rates down under 5% and maybe, in ideal situations, closer to 1%. This is a significant risk reduction because the percentage is small, right?
Phishing attacks are just the entry point into your organization. They only need one victim to be successful as that one compromise gives them a foothold – a user account, a connected system, network access – from which to spread. In other words, one click and one infection means the attack was successful.

For each phishing attack, a 1% click rate means:
- 9% chance someone is infected in a 10-person company
- 63.4% chance someone is infected in a 100-person company
- 99.996% change someone is infected in a 1,000-person company
Reducing the likelihood that your employees fall for digital scams, including clicking on phishing messages, is a good thing and will reduce your organizations risk. However, it will never fully protect you and should be your last line of defense not your primary or only defense against phishing attacks.
The Cloud Paradox
Ironically, our move to online shopping, cloud services and modern applications has increased our reliance on email in the worst possible way. These services leverage email to communicate and distribute information, typically as links and attachments – the same links and attachments we’re training everyone to avoid.
How big is this problem? Anecdotally – I looked at my own email for one day. Of the messages delivered into my inbox that were not malicious and not spam, about 20% had legitimate attachments and 40% had active links. Think about your own enterprise and how much “legitimate” email goes around with links and attachments such as HR (eg. tax & open enrollment) and IT (eg. password reset, software activation) communications as well as alerts from your cloud platforms (eg. “Someone shared a file with you”, “this task has been updated”). This highlights the fundamental contradiction in most organizations – using email to enable more self-service workflows while telling people that they should be wary of email. Is it a big surprise that they clicked on that OneDrive file share email?
It’s about the message
I recently ran a phishing test at a company who had not run one in a while. The result was ~20% click rate. On the surface, the click rate seems high but not uncommon for a company who isn’t running regular tests nor doing in depth training.
What’s the typical response? Increase the intensity of the phishing campaign, push more people through more training, identify repeat clickers and put them through even more training, etc. What will this training teach: Phishing messages have four typical properties:
- There is a sense of urgency
- They ask you to undertake an unusual or unexpected action
- They have suspicious characteristics like misspellings, bad grammar, etc.
- They use domains, sender email, or link addresses that look odd
We took a different approach and looked not at who was clicking but what they were clicking. We sent about 1,000 messages spread equally across three templates. Two of the templates had a 3-5% click rate. The third template had a 60% click rate. The third template was a simulated OneDrive file sharing notice at a company that is a very heavy user of OneDrive. When we re-ran the test without a OneDrive template, the overall click rate was under 5%.
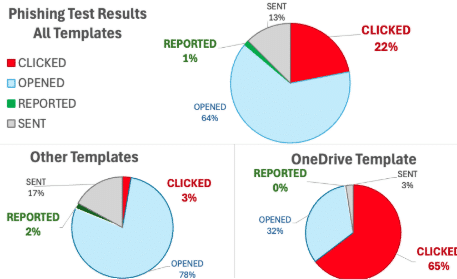
In fact, our community was generally well-trained, and more generic training would have been ineffective. The problem was that the OneDrive template matched a routine workflow that we encourage – OneDrive file sharing. This template was properly formatted, with a typical action (click to see the shared file), and no urgent call to action (beyond curiosity). Was the link and domain odd or unusual – do you know what the standard URL structure and email sender is for a OneDrive share?
From Blame the Human to Block the Message
Email was not originally designed for security… but it’s getting there. If you want to improve your email security and get beyond reliance on user behavior, awareness training, focus on technical controls to limit or block malicious emails.
Email Authentication:
The first step is with a proper DMARC configuration for both inbound and outbound email. DMARC allows you to tell the world where legitimate messages from you originate and for you to identify spoofed messages. Most major consumer email platforms are starting to require this so your messages will increasingly be blocked if you don’t fully and properly implement DMARC (See “Time to Get Strict With DMARC”).
- Configure your DMARC policy to REJECT for all your domains, including the “parked” domains you own but don’t use.
- Configure your email gateway to honor and drop inbound messages that fail a DMARC or SPF check.
Message Cleansing:
If you are going to deliver a message from the outside, make sure it’s clean. This will require you to have some form of secure email service or configuration that can at least do the following:
- Clearly mark all inbound emails from the outside with an “EXTERNAL” flag
- Actively rewrite URLs so access is dynamically check by every time its clicked
- Block uncommon attachment types and disable automatic image downloads
- Implement attachment sandboxing before delivery
Control Delivery
You don’t need to deliver ever email immediately for everyone.
- Adjust quarantine thresholds based on user roles and risk profiles
- Quarantine first time senders or messages from uncategorized domains
Continually Improve
Your community clicks on phishing tests and reports suspicious emails, which tells you which messages are most likely to lead to a compromise. You should analyzing these messages to improve your filtering, so they don’t get through next time, not just to create “better” phishing templates more likely to trick your community into clicking.
- Collect and analyze messages reported by your community as phishing and use those to improve your filtering
- Subscribe to professional message analysis services rather than relying on your overworked IT staff who may not be trained on email analysis
The Nuclear Option: Eliminate Internal Email
“The only winning move is not to play.”

WOPR. WarGames (1983).
Hadas Cassorla, one of our principal consultants, wrote in her recent article “From Inbox Zero to Zero Inbox“:
We don’t actually need email for internal business communications.
Here’s the most radical recommendation:
Stop using email for internal communications
This isn’t fantasy – this is achievable if you focus on these three things
- Move communication from Email to Chat
Almost every organization has deployed one or more internal communications platforms – Teams, Zoom, Slack, etc. – so start enforcing their use for internal communication. Begin by identifying email-based workflows and replacing them with integrations or actions via your chat platform. This will decrease email, especially email with attachments and links, while also helping you implement and enforce your email retention policy.
- Use centralized data storage
Like chat, almost every organization has a centralized file store such as OneDrive or GDrive. This is where files should live, not in email. Instead of emailing attachments, you need to train and require everyone to upload documents to this file share and then share the link via chat platform. In addition to email safety, this will also help with your overall data lifecycle management.
- Build and use your Intranet
Modern intranet solutions are trivial to implement, especially with existing GSuite or Office 365 subscriptions. You can replace most internal broadcast communication with content and links on your Intranet then tell people where to find it via Chat.
This approach creates a clear boundary: any email received is external and should be treated with appropriate suspicion.
The Path Forward
The people within our organizations are an important and critical component of our security posture. They need training on how to spot, avoid, and properly respond to cyber threats. However, security programs should also emphasis process and technological solutions to prevent email compromises. Programs should focus on implementing secure email configurations and technologies then invest in process improvements that both continually improve email filtering while also reducing and eliminating workflows that that rely on people to click links in an email.


