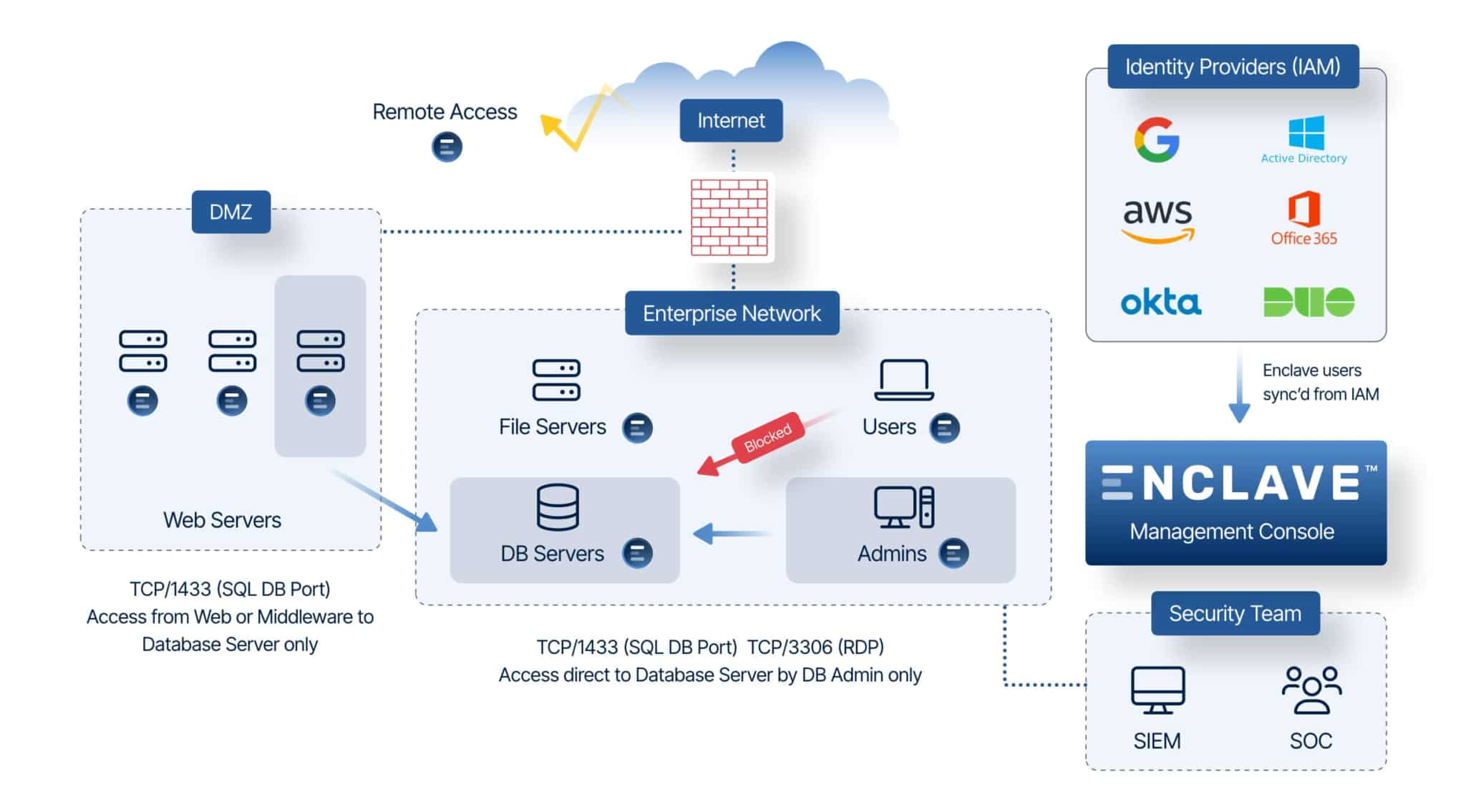
Enclave for Enterprise & SMB
Traditional security measures are no match for sophisticated cyber attacks. That’s where Enclave steps in. Purpose-built to secure and segment networks, Enclave combines access control, asset inventory, encryption, and Zero Trust network access to bolster your defenses.