Cloud Misconfigurations: A Hidden Cybersecurity Risk
Cloud technology has revolutionized business operations, offering scalability, flexibility, and cost savings. However, it also brings a major security challenge: misconfigurations. These errors—often caused by human oversight or lack of expertise—are now a leading cause of cloud breaches. For executives, addressing misconfigurations is crucial to protecting organizational assets.
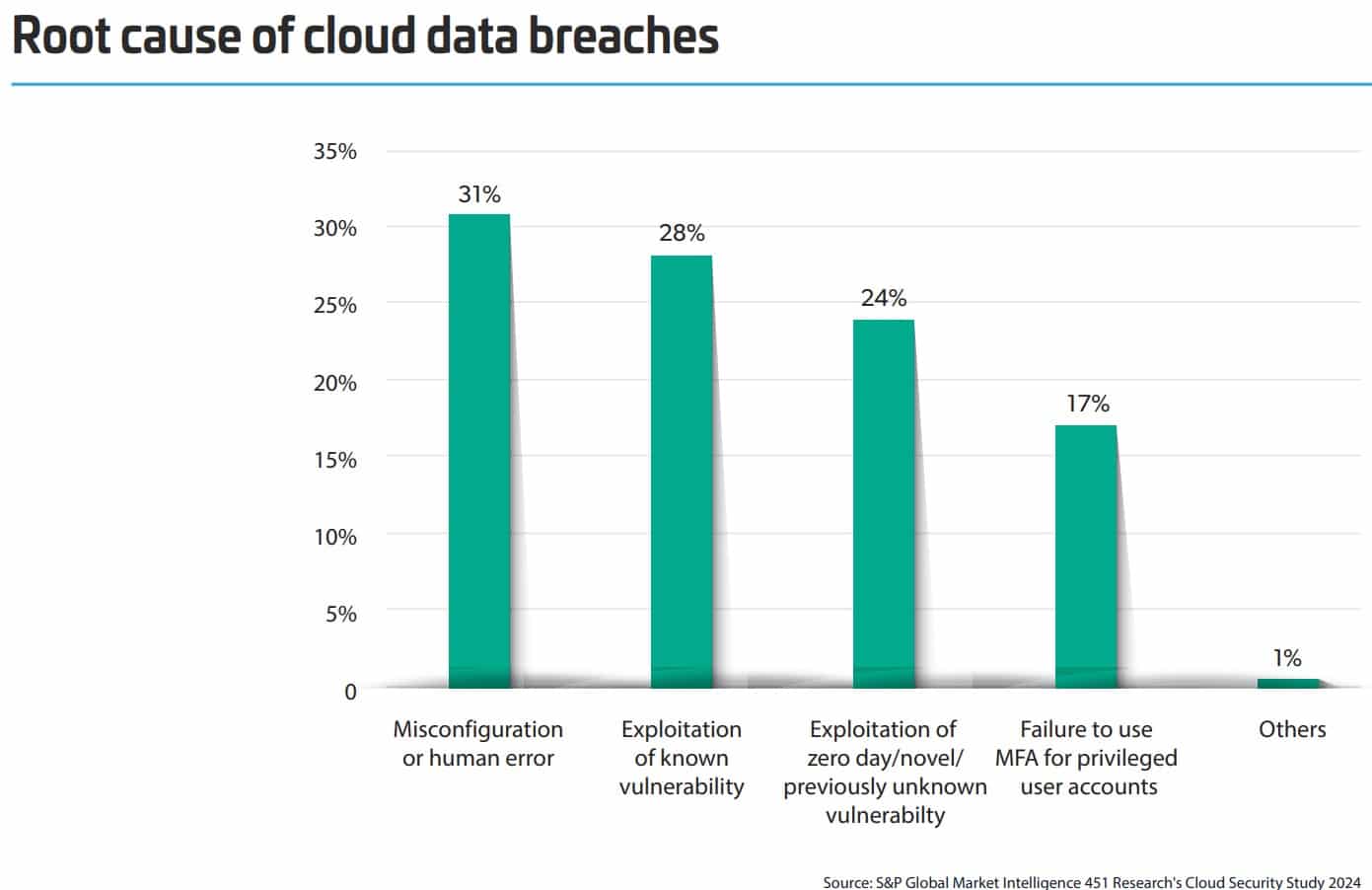
The Growing Threat
Cloud misconfigurations occur when security settings are misapplied or missing, which exposes systems. Common risks include:
- Open storage buckets leaking sensitive data
- Weak identity & access controls allow unauthorized access
- Unencrypted data vulnerable to interception
Aqua Security reports that 90% of multi-cloud environments are susceptible to breaches due to misconfigurations, yet less than 1% of enterprises fully remediate issues. Compounding this problem, developers often prioritize speed over security, and shadow IT—unauthorized cloud deployments—creates unseen vulnerabilities.
Why Misconfigurations Persist
Several factors contribute to this ongoing risk:
- Cloud Complexity: Managing security across hybrid and multi-cloud environments is overwhelming.
- Siloed Teams: Lack of coordination between DevOps and security teams creates blind spots.
- Identity Risks: With no physical perimeters, weak IAM policies, and stolen credentials become prime attack vectors.
- Lack of Clear Strategy: Focusing on speed or cost savings without determining which workloads should be hosted in the cloud.
The Consequences
Unchecked misconfigurations can lead to:
- Data Breaches – Exposed storage and databases leak sensitive information.
- Resource Hijacking – Attackers exploit open APIs and ports for malicious activities like crypto mining.
- Operational Disruption – Exploits lead to denial-of-service (DoS) attacks and downtime.
- Poor Business Outcomes – Without strategic alignment that delivers business outcomes your cloud migration can be perceived as friction.
According to CrowdStrike, cloud intrusions rose by 75% from 2022 to 2023, with misconfigurations being a key target.
How to Reduce Your Risk
Organizations must take a proactive approach to mitigate misconfiguration threats:
✔ Enhance Visibility – Use real-time monitoring tools to detect vulnerabilities across cloud environments.
✔ Prioritize Risk Management – First, focus on fixing the most critical security gaps based on business risk.
✔ Strengthen Identity Controls – Enforce least-privilege access and multi-factor authentication (MFA).
✔ Integrate Security into DevOps – Embed security checks into development workflows.
✔ Adopt Defense-in-Depth Strategies – Layer security defenses to catch threats in real-time.
Hot Tip:
Focus on updating and validating your cloud Identity and Access Management policies and profiles during your initial adoption of cloud services. Cloud services scale quickly and re-doing Identity and Access configurations later will slow your projects by 30% or more!
Next Steps
Cloud misconfigurations are a silent but serious risk. Don’t leave your organization exposed. Contact the SideChannel team for a free cloud security architecture review to ensure your cloud environment is secure from hidden threats.


