Many organizations historically saw cybersecurity as a complex and unmanageable challenge. With the fear, uncertainty and doubt surrounding the issue, organizations felt stuck. Add compliance and breach reporting requirements, and changing legislation, and businesses without a dedicated security executive and team, simply can’t keep up. We’re here to change that.
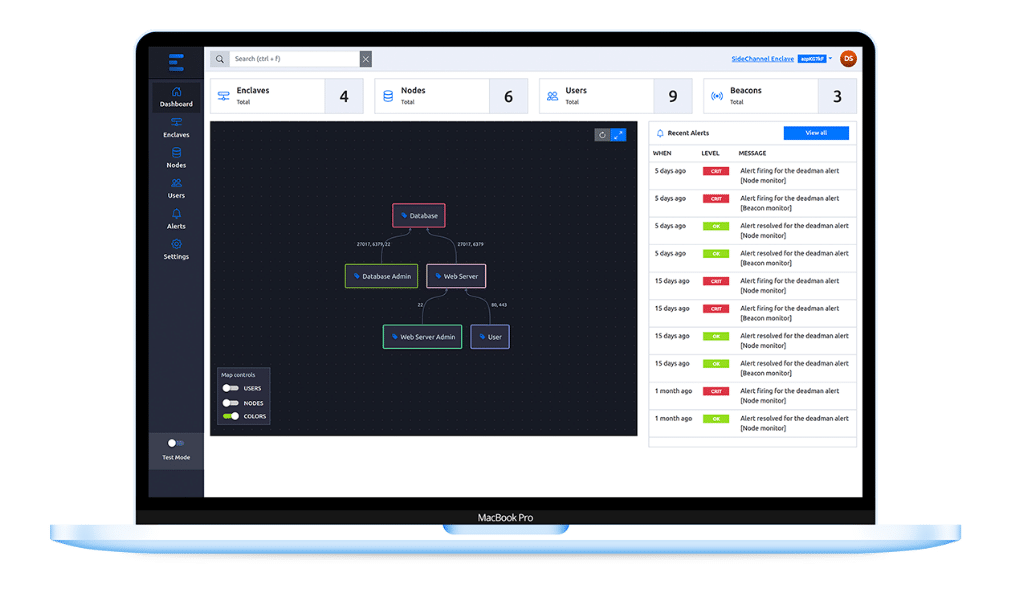
We’re delivering cybersecurity services differently. Rather than offering point solutions or traditional outsourced detection and response, we’ve developed a new way to guide organizations to implement a functional and effective cybersecurity program. That’s SideChannel Complete.
With SideChannel Complete you’re able to implement a program that meets the needs of your organization, fits your tech stack and workflows, and meets compliance standards that are elevant to your industry. It’s the fastest and most effective way to be proactive about security.